Looking at SAML In 2023 !
What is SAML
SAML stands for Security Assertion Markup Language. It is an XML-based open-standard for transferring identity data between two parties: an identity provider (IdP) and a service provider (SP).
SAML basically asks as a link between the authentication of a user’s identity and the authorization to use a service.
SAML, created by OASIS, remains the dominant standard among the various standards existing in the world of Federated Identity Management. The common goal among these standards is to enrich the user experience and enhance security.
SAML enables web browser SSO by allowing users to sign in to apps/services with a single set of credentials. This centralization not only provides convenience to employees but also improves organizational security, among other benefits.
One of the bigger challenges in the tech world is make sure that applications, products,Saas/PaaS solutions, cloud solutions etc built by different vendors and companies for different purposes, they work together seamlessly as a Unit. This is known as Interoperability, it refers to the ability of apps, equipment, products, and systems from different companies(vendors) to seamlessly communicate and process data in a way that does not require any involvement from end-users.
So SAML is an interoperable standard — it is a widely accepted way to communicate a user’s identity to different service providers.
SAML does two key functions:
- Authentication: determining and ensuring that users are “who they claim to be”.
- Authorization: passing user authorization to applications for access to certain systems or content.
How does SAML work?
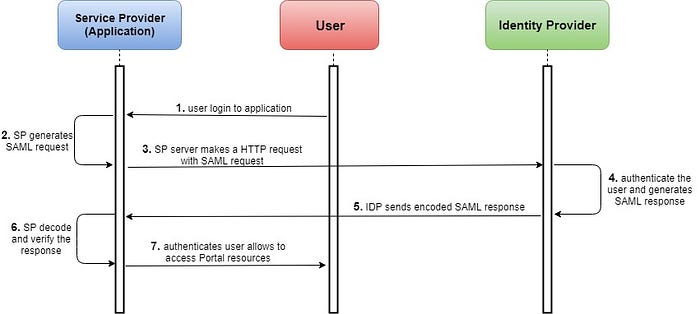
As per wikipedia: “The SAML specification defines three roles: the principal (typically a human user), the identity provider (IdP) and the service provider (SP).In the primary use case addressed by SAML, the principal requests a service from the service provider. The service provider requests and obtains an authentication assertion from the identity provider. On the basis of this assertion, the service provider can make an access control decision, that is, it can decide whether to perform the service for the connected principal.”
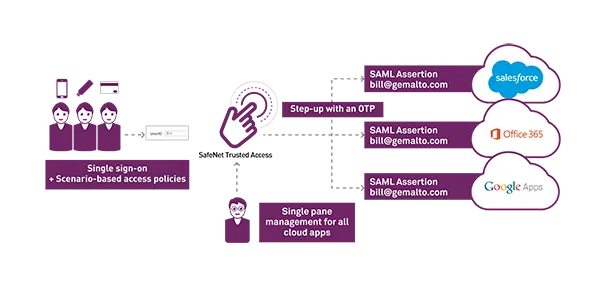
With SAML SSO, the users do not log into the applications directly. Instead, they log into an SSO based platform. When a user himself authenticates successfully, SAML gives that user access to multiple resources across multiple domains.
What is a SAML assertion?
SAML assertions are noting but XML documents sent from an IdP to an SP which identify users, and contain pertinent dat about them, and specify their privileges in the target application or service.
There are three types of SAML assertions:
- Authentication assertions: these assertions are generated by the system that authenticates a user and contain information about how the authentication decision transpired and log information including timestamps.(Eg.password, MFA, Kerbeos, etc.)
- Attribute assertions: it passes the SAML attributes to the service provider — SAML attributes are specific pieces of data that provide information about the user.The attribute used by SAML to identify the user is assumed to be the same in both the IdP and SP directory.
- Authorization assertions: an authorization decision assertion says if the user is authorized to use the service or if the identify provider denied their request due to a password failure or lack of rights to the service.
SAML & SSO:
Even though SAML was designed keeping in mind a wide range of use cases , but the most common one in practice is Single-sign-on(SSO). SSO, as the name implies, allows a user to log in once and then access multiple services — websites, cloud solutions or SaaS apps and so on. In an SSO scenario, all these services outsource their authentication and authorization functionality to a single system that then sends identity information about the user to those services.
SAML Single Sign-On is a mechanism that leverages SAML allowing authenticated users to log on to multiple web applications and systems, after logging into the identity provider. As the user only has to log in once, SAML SSO provides a faster, seamless user experience.
Benefits of SAML
- Improved user experiences : SAML not only makes it easier to log in to applications and services, but also helps users be more productive because they can readily access the tools they need to get their jobs done.
- Greater security: SAML provides a single point of authentication at a secure identity provider, which then transfers the user’s identity information to service providers. This ensures that credentials are only sent directly, minimising opportunities for phishing or identity theft.
- Reducing costs: implementing SAML saves significant amount of time for IT admin related activities, as it helps to eliminate the need for new ticket creation, submission password reset etc. It also helps to keep development costs to a minimum.
- Single source of identity. when an employee joins or leaves a company, you don’t have to worry about the myriad of internal services that now have to be updated, and the ones that will inevitably be missed.
- Interoperability — as SAML is an open standard, it makes interoperability possible between diverse systems.
- Platform neutrality — SAML decouples the security framework from platform architectures and vendor-specific implementations. It supports service-oriented architecture (SOA) by making security less dependent on application logic.
- Easy Access of Applications — Logins are easier to remember and more convenient. Users can effortlessly sweep through applications without spending time with required logins.
Recent Post
- Finding the Best Gambling Sites: Your Guide to Safe and Enjoyable Play
- Die top deutschen Sportwetten Anbieter im ausführlichen Vergleich und Test
- Как именно собственные цели влияют в рамках оценку достижения
- How to Download and Use the Aviator App in India
- Siti di casinò online non AAMS: Il significato della regolamentazione internazionale nel mantenere la sicurezza.
- Comment détecter un casino en ligne fiable pour jouer en toute sécurité

